Cyber tdx is developing an open ecosystem to help routers and gateways better protect the network against IOT attacks. This approach complements other initiatives which are enhancing IOT endpoint security. Cyber tdx accepts the fact that there are many insecure IOT devices already in the market, which are not going away any time soon. In addition, even the best IOT endpoint security can and will be compromised. Enhancing the role that the gateway can play in the detection and protection against IOT attacks is and always will be a valuable addition to a comprehensive security strategy.

Dynamic Risk
Multi factor 360 degree risk assessment using type and instance data.

Lifecycle Management
Full integration with procurement and servicing on a fully distributed basis.
Cyber Data Sources
Integrates with well known and novel data cyber sources using standard interfaces (D3).

Cognitive Security
Reason under uncertainty. Practical Zero Trust. Controllable false positive.

Collaborative
Share data between instances and organisations to better detect and respond.

Integration
API first design using distributed security makes it easy to integrate with legacy and partner systems.
distributed device descriptors
The Distributed Device Descriptors (D3) workstream addresses a number of problems:
- How does a community make statements about device types, reliably and securely?
- How can the community reason about devices reliably, whether this reasoning is human-centric or machine-centric?
D3 provides structured data of known provenance, which can be used to assert claims about how IoT devices should behave
destination-based anomaly detection
These images show graphical representation of the device’s destination requests on the network and the policy produced by applying the destination-based anomaly detection model
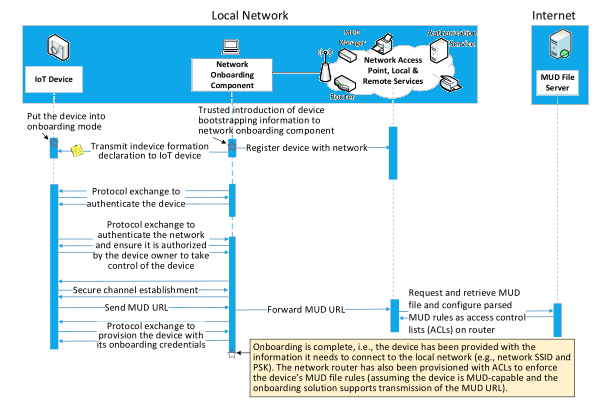
lifecycle management
To be strongly authenticated, the device asserts a specific identity, and that identity is cryptographically bound to the device. In some onboarding situations, a device may not be asserting a specific identity; instead, it may simply be asserting to be a particular type of device or to be from a particular manufacturer. In such cases, it is not possible to authenticate the device, though it may be possible to verify device type.